How to securely store cryptographic keys images are ready in this website. How to securely store cryptographic keys are a topic that is being searched for and liked by netizens today. You can Find and Download the How to securely store cryptographic keys files here. Find and Download all royalty-free photos.
If you’re looking for how to securely store cryptographic keys pictures information connected with to the how to securely store cryptographic keys interest, you have visit the ideal blog. Our website frequently gives you suggestions for seeking the maximum quality video and image content, please kindly hunt and find more informative video articles and graphics that fit your interests.
Implement role segregation-Make sure that there is controlled access for those who need to use the cryptography keys. For Secret permissions select Get and List. Keep the cryptographic keys hidden in a safe digital vault. Manage Cryptographic Keys and Secrets in Az. User must not have access to App1 key.
How To Securely Store Cryptographic Keys. 26032018 Here are six key pun intended considerations to help secure and protect cryptographic keys. An example of this that you may be familiar with is Microsoft Azures Key Vault which can safeguard your cryptographic keys in Microsofts own cloud HSM. 27052021 Azure Key Vault provides the capability to import store and manage cryptographic keys and certificates that can be securely accessed as needed. Ive seen setups where the data is stored encrypted with the key stored on a thumb drive thats attached nightly to run the batch process but this is an incredibly flimsy and manual.
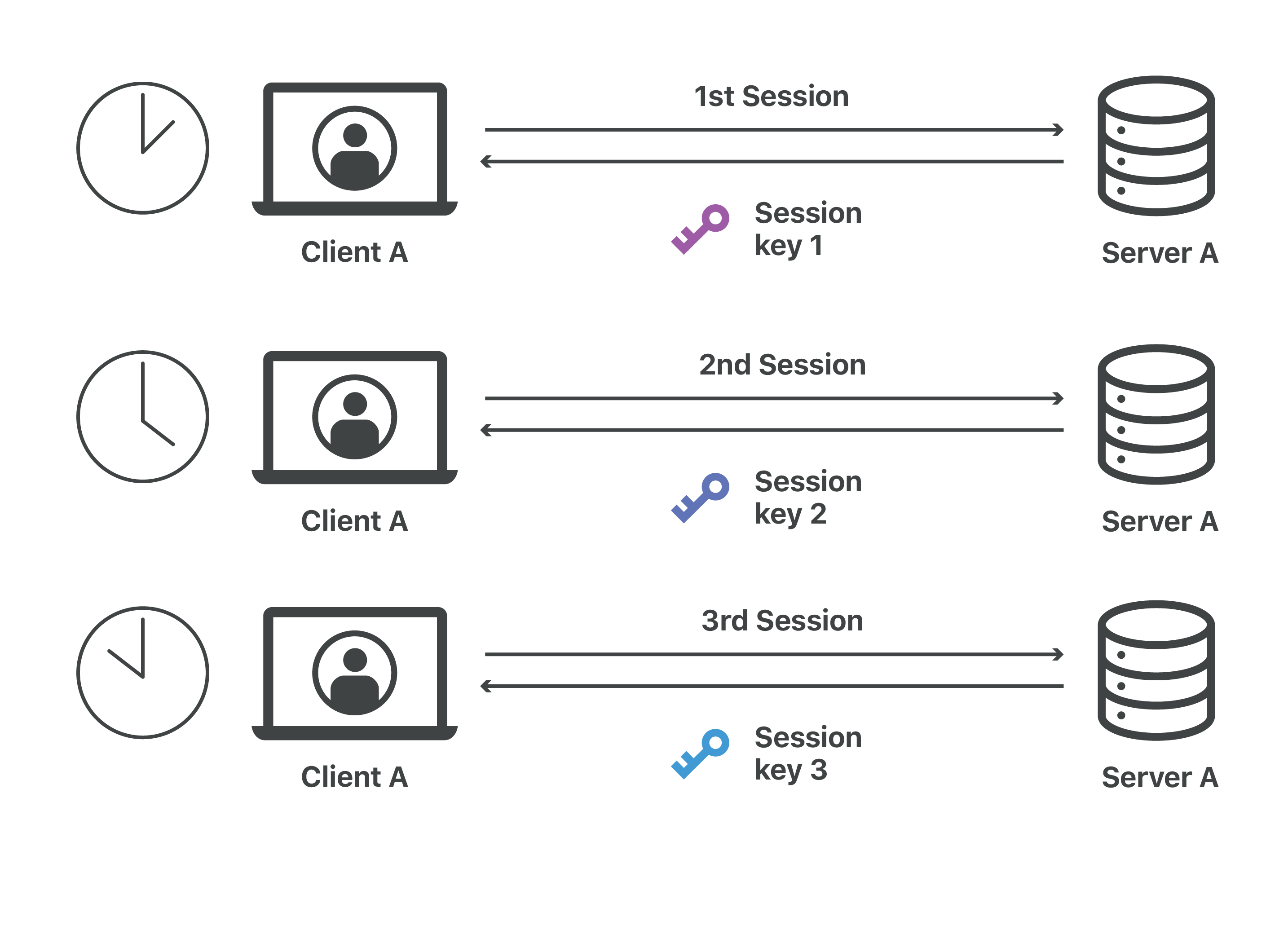 What Is A Session Key Session Keys And Tls Handshakes Cloudflare From cloudflare.com
What Is A Session Key Session Keys And Tls Handshakes Cloudflare From cloudflare.com
For encrypting local data developers should construct secret keys using cryptographically secure randomness or from user generated data if using PBEKeySpecs and store. Then it can be found. Store the key on a different server. In your projects root directory. This topic shows how to do the following. Create a Key Vault to securely store sensitive information.
26032018 Here are six key pun intended considerations to help secure and protect cryptographic keys.
Manage Cryptographic Keys and Secrets in Az. User must not have access to App1 key. Secure application access should be enabled- access to. Store the key elsewhere on the same server. For encrypting local data developers should construct secret keys using cryptographically secure randomness or from user generated data if using PBEKeySpecs and store. For Secret permissions select Get and List.
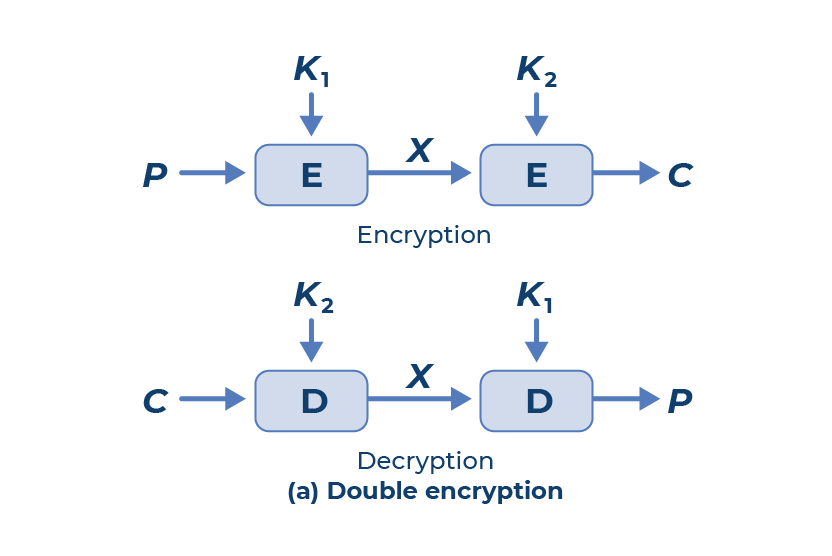 Source: advantio.com
Source: advantio.com
Manage Cryptographic Keys and Secrets in Az. Manage Cryptographic Keys and Secrets in Az. And create a new file named keystoreproperties. If you are a smaller organization without the ability to purchase and manage your own HSM this is a great solution and can be integrated with public CAs including GlobalSign. For Secret permissions select Get and List.
 Source: in.pinterest.com
Source: in.pinterest.com
User must not have access to App1 key. Store the key elsewhere on the same server. Welcome to the How to Securely Create Cryptographic Keys. Configure your e-commerce site to securely communicate with Retail Server. Store the key.
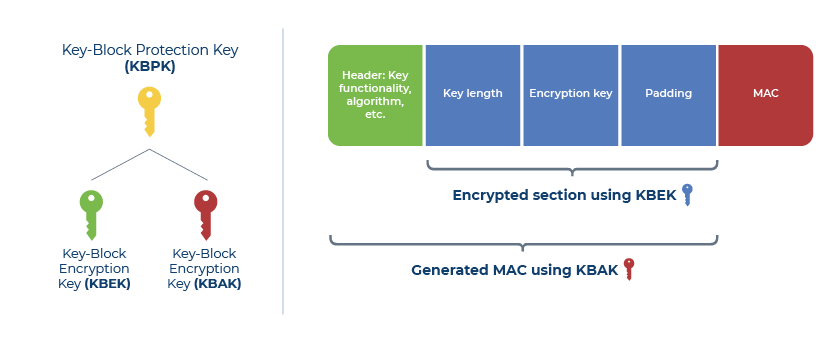
 Source: encryptionconsulting.com
Source: encryptionconsulting.com
Android store token in keystore. Introduce role segregation Control individual access to stored keys preventing even. This presentation was delivered on Thursday August 29th 2019In this class. 26032018 Here are six key pun intended considerations to help secure and protect cryptographic keys. Store the key elsewhere on the same server.
 Source: pinterest.com
Source: pinterest.com
Storing keys without proper protection could provide access to attackers resulting in the decryption and exposure of cardholder data. Store cryptographic keys in a secure digital vault Move keys into a digital vault with multiple layers of security. For Secret permissions select Get and List. The security keys should be stored in a digital vault that. Configure your e-commerce site to securely communicate with Retail Server.
 Source: pinterest.com
Source: pinterest.com
A follow-up on how to store tokens securely in Android But we want to provide an additional security layer. This presentation was delivered on Thursday August 29th 2019In this class. 04102011 This requires we store customer credit card data for as long as a week worst-case if theres an outage etc. An example of this that you may be familiar with is Microsoft Azures Key Vault which can safeguard your cryptographic keys in Microsofts own cloud HSM. Store cryptographic keys in a secure digital vault Move keys into a digital vault with multiple layers of security.
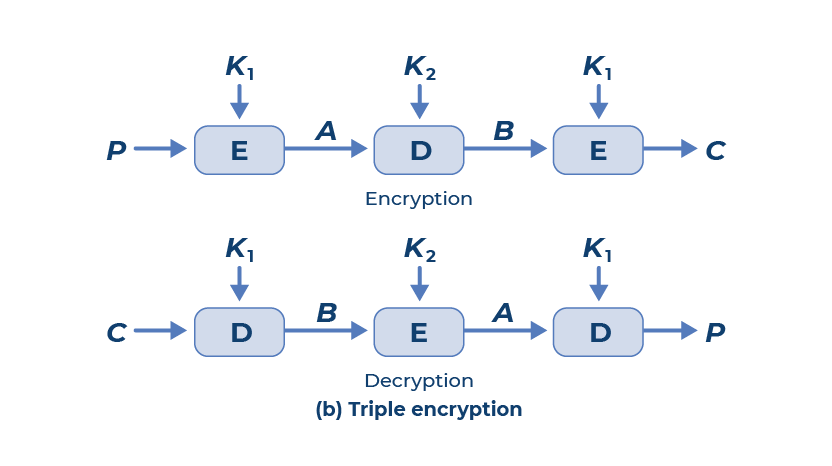
 Source: advantio.com
Source: advantio.com
If you are a smaller organization without the ability to purchase and manage your own HSM this is a great solution and can be integrated with public CAs including GlobalSign. Implement role segregation-Make sure that there is controlled access for those who need to use the cryptography keys. Select the option to select a service principal and search for the one you created in the beginning of this section. Introduce role segregation Control individual access to stored keys preventing even. Ive seen setups where the data is stored encrypted with the key stored on a thumb drive thats attached nightly to run the batch process but this is an incredibly flimsy and manual.
 Source: encryptionconsulting.com
Source: encryptionconsulting.com
27052021 Azure Key Vault provides the capability to import store and manage cryptographic keys and certificates that can be securely accessed as needed. Secure application access should be enabled- access to. Typically its better that you memorize the recovery phrase in order to be able to recover your funds at any time. For encrypting local data developers should construct secret keys using cryptographically secure randomness or from user generated data if using PBEKeySpecs and store. Select the option to select a service principal and search for the one you created in the beginning of this section.
 Source: pinterest.com
Source: pinterest.com
Store the key elsewhere on the same server. Then it can be found. If you are a smaller organization without the ability to purchase and manage your own HSM this is a great solution and can be integrated with public CAs including GlobalSign. The security keys should be stored in a digital vault that. Type in the encryption key when you start up store it in memory.
 Source: advantio.com
Source: advantio.com
04102011 This requires we store customer credit card data for as long as a week worst-case if theres an outage etc. And create a new file named keystoreproperties. Create a Key Vault to securely store sensitive information. Type in the encryption key when you start up store it in memory. Secure application access should be enabled- access to.
 Source: encryptionconsulting.com
Source: encryptionconsulting.com
Secure application access should be enabled- access to. Then it can be found. Ive seen setups where the data is stored encrypted with the key stored on a thumb drive thats attached nightly to run the batch process but this is an incredibly flimsy and manual. Store the key on a different server. For Secret permissions select Get and List.
 Source: pinterest.com
Source: pinterest.com
04102011 This requires we store customer credit card data for as long as a week worst-case if theres an outage etc. Store the key on a different server. You could also do some research about a so-called mnemonic pegging technique and create a brain wallet. Manage Cryptographic Keys and Secrets in Az. Android store token in keystore.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how to securely store cryptographic keys by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





